Microsoft SSO
Overview
The "Microsoft Multi-Tenant SSO" functionality enables users to sign into the Cloudmore platform using their Microsoft credentials, streamlining access for those who prefer a unified authentication process across multiple platforms.
This feature minimizes the need to remember multiple sets of credentials, while enhancing security by leveraging Microsoft’s Single Sign-On (SSO) capabilities.
It is especially beneficial for Microsoft partners who manage multiple tenants or frequently access other platforms with their Microsoft accounts.
In addition to enabling Microsoft SSO for Broker and Organization users to log in with their Microsoft credentials, you can also enforce Microsoft SSO for all Broker and Organization users.
Enabling Microsoft SSO
Microsoft SSO can be enabled from the Security Center page. To perform this action, the user must have the Cloudmore Broker Super Admin role, as it provides full access to the Security Center. The Broker Global Admin and Broker Global View Only Admin roles have read-only access.
To enable Microsoft SSO, follow these steps:
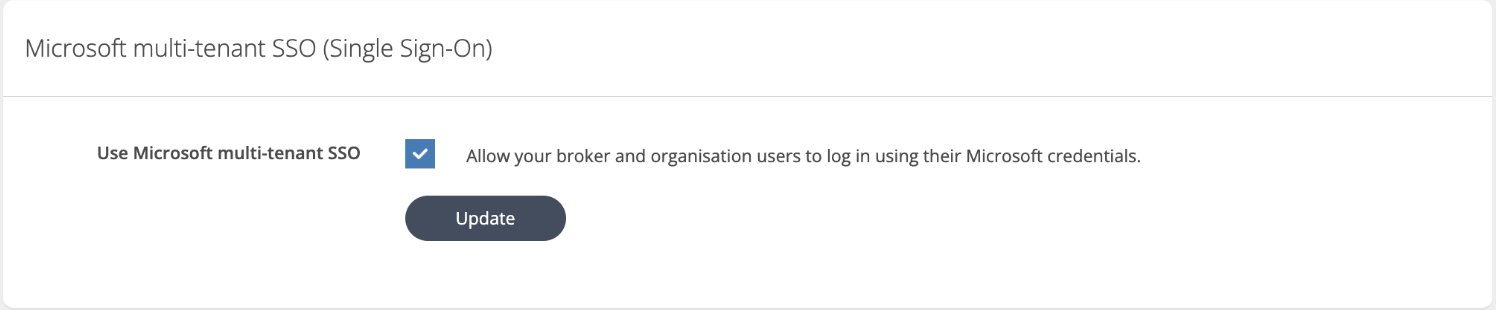
Navigate to the Security Center page under the Broker menu.
Select the checkbox for "Use Microsoft Multi-Tenant SSO" to allow Broker and Organization users to log in using their Microsoft credentials.
Click "Update" to apply the changes.
Enabling the Microsoft SSO adds the ‘Sign in with Microsoft’ button on the main
page if you have a branded URL configured.
If you don’t have a branded URL, the button will be visible all the time, but the sign-in will
work only after the functionality has been enabled.
Enforcing Microsoft SSO
You can enforce Single Sign-On (SSO) for all Broker and Organization users. If both Microsoft and SAML-based SSO options are enabled, users will have the flexibility to log in using either method. The enforcement of SAML-based SSO will be applied at the organization level, provided it is enabled for the respective organizations.
To enforce SSO, follow these steps:
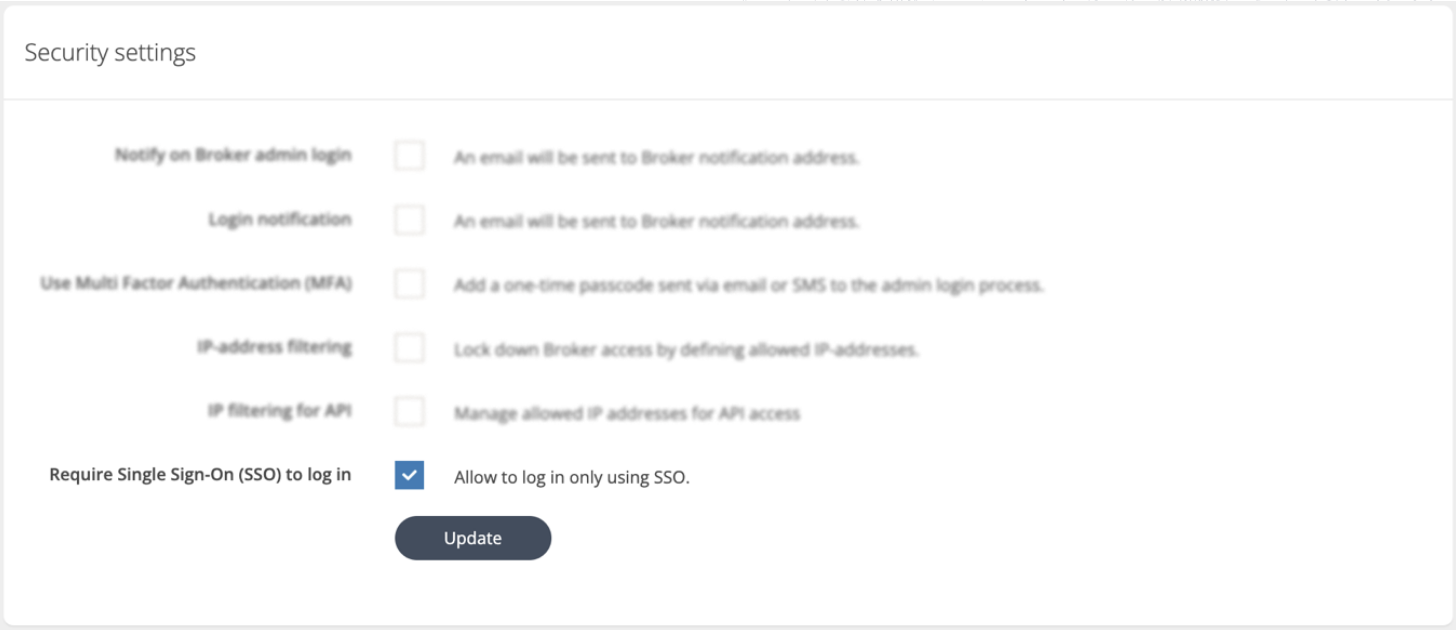
Check the box labeled "Require Single Sign-On (SSO) to log in" under the Security Settings section.
Click "Update" to apply the changes.
Rolling out Microsoft SSO
When creating Broker users and Organization users, and the Microsoft SSO is enabled, the password email will not be sent, and the Cloudmore MFA will be ignored.
When you turn off the Microsoft SSO and want users to be able to log into Cloudmore using passwords, then these must be configured manually or programmatically using APIs.
Use your own white-labelled Azure application for sign-in (optional, branded brokers only)
Since your customers’ admins will need to provide consent to use the application, you may want to create and publish your own application in the Azure portal for a more seamless white-labeling and governance experience. This option is available for the Brokers who use a branded URL page.
Once a broker with branded login enables Microsoft multi-tenant SSO, additional fields will appear for entering details of their own Azure application. By default, if these fields are left blank, Microsoft
sign-in authorization will be handled by the Cloudmore application, where Cloudmore will appear as the publisher.
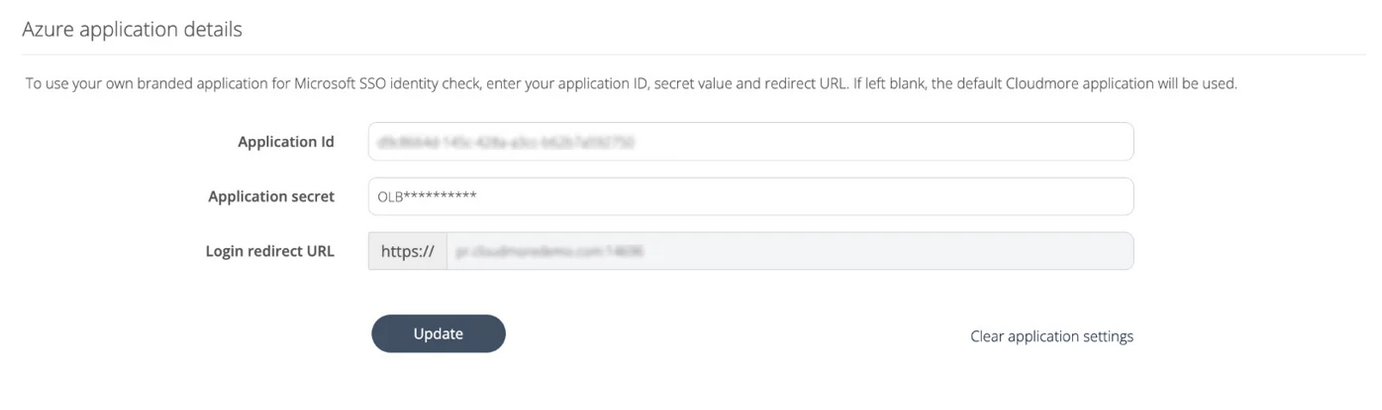
Enter your Azure application ID in the “Application ID” field.
Enter your Azure application secret in the “Application secret” field.
The login redirect URL is populated automatically and is the same as the Branded URL from your Cloudmore Broker -> Branding -> Branded login page.
Click "Update" to apply the settings.
*Your application details will be encrypted and securely stored in Cloudmore.
Clicking “Clear application settings” button will remove the application details completely from the Cloudmore database.
REQUIREMENTS FOR THE AZURE APPLICATION
When creating your Azure application, make sure that it has the following properties:
Authentication - Supported account types: Accounts in any organizational directory (Any Microsoft Entra ID tenant - Multitenant)
API permissions: User.Read
Authentication - Redirect URIs: add your Cloudmore Branded URL in the list
Log in Using Microsoft SSO
Once Microsoft multi-tenant SSO is enabled, Broker and Organization users will be able to
use the "Sign in with Microsoft" option to log in to the Cloudmore platform.
In order to successfully log in using Microsoft SSO, the user's "Username" in
Cloudmore should match the email address used for Microsoft authentication.
Click the "Sign in with Microsoft" button on the main page.
You will be redirected to the Microsoft authentication screen where you can enter
your Microsoft credentials.
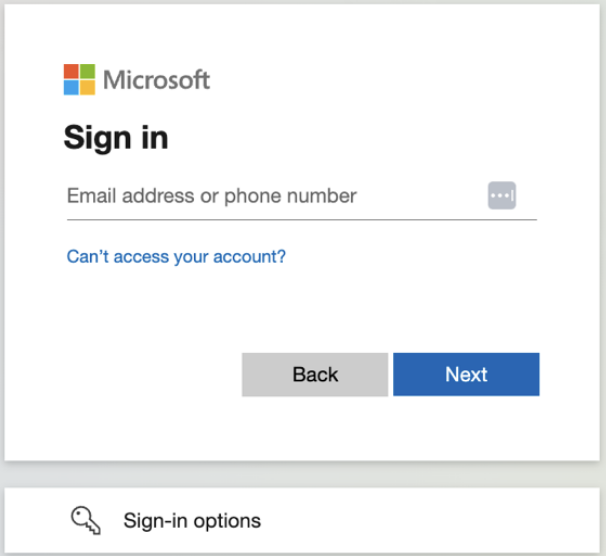
Upon successful Microsoft authentication, you will be redirected back to the
Cloudmore platform, where the system will verify the authentication response and
logs you in.
Best practices
Ensure all users have matching usernames: Make sure the email used for Microsoft authentication is the same as the user’s Cloudmore username.
Enforce SSO strategically: If enforcing SSO, ensure all users are informed about the changes and have set up their accounts correctly. It’s recommended to enable SSO during a time of minimal system activity to avoid disruption.